Get started with Incognitee Test Net
Incognite Paseo Test Wallet
You can already test a simple version of the Incognitee Wallet on Paseo. Follow the link : https://try.incognitee.io
Once you enter the website, you will see the Incognitee wallet, which is already generating new wallet for you.
The first step is to obtain free PAS tokens on Paseo via the button below in the window. There you should copy the address into your clipboard and go to the Paseo faucet.

Enter your copied wallet address in the faucet to get your first 100 free PAS. After this, you can close this window and return to the Incognitee web wallet.

You can now also close the pop-up screen and continue interacting with the wallet. Now you can also see on the top, that you are currently active on the only available test network Paseo with one available Token PAS. In the center of the screen, you can see your current public balance, as you just retrieved 100 PAS from the faucet. From here you can now either shield your balances to the private L2 or switch to your private balance.

By selecting "Shield" you can now transfer your PAS to the private L2 layer.

Switching now to the private balance, you can either send or receive PAs tokens privately and instantly without leaving any trace on chain. Or you can unshield the PAS tokens back to layer 1.

Under the hood
Check sidechain activity
Visit the Integritee Network on Paseo explorer where you can see events whenever sidechain blocks get finalized:
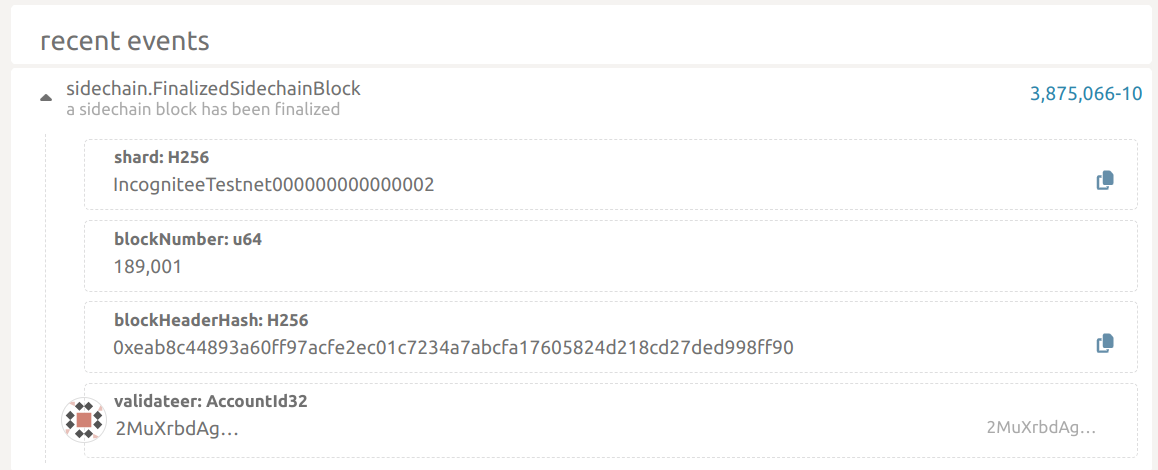
As privacy is our main feature, you can’t see much more here. The BlockHeaderHash helps you proving that you sent funds to someone. By default, recipients just observe a change in their balance but they have no clue where the funds come from unless you tell them and provide a merkle proof for the sidechain block inclusion of your transfer.
However, as shielding and unshielding events are publicly happening on Paseo, you can observe shielding/unshielding activity on the vault account on subscan.
The balance of the vault account will always exactly match the total supply on the respective sidechain shard.
What are shards and mrenclaves?
Each instance of an Incognitee sidechain is identified by a shard identifier and we’ll need to tell the validators which shard we’d like to talk to. Think of it like the genesis hash of a L1 blockchain.
The MRENCLAVE identifies the validator code which is executed in Intel SGX enclave (it’s basically the hash of the enclave binary). Your call will only execute if the validator runs the code you expect it to run.
Why should I trust validators?
Because they can’t cheat and they can’t see your data. That’s what TEEs guarantee. But how should you know that the validators actually run the correct code in a TEE? You can authenticate validators thanks to Integritee’s remote attestation registry at enclaves.integritee.network.
There you can find the validator for this tutorial if you search for the url you’re using wss://integritee-1.cluster.securitee.tech:2000 and it will tell you the verified MRENCLAVE which has been remotely attested using our decentralized DCAP process.
Last updated